We're maturing Cyber-Security to Digital-Safety
by protecting individuals, institutions and communities.
We help enterprises engineer resilient, human-centric systems, where safety is designed, not assumed. Our expertise bridges technology, people, and risk, ensuring your products are prepared for the realities of today’s interconnected world.

"Just like a quantum bit (qubit) your cyber-security posture is in a state of superposition, you can be both secure and vulnerable at the same time. It's only when measured that you truly know..."
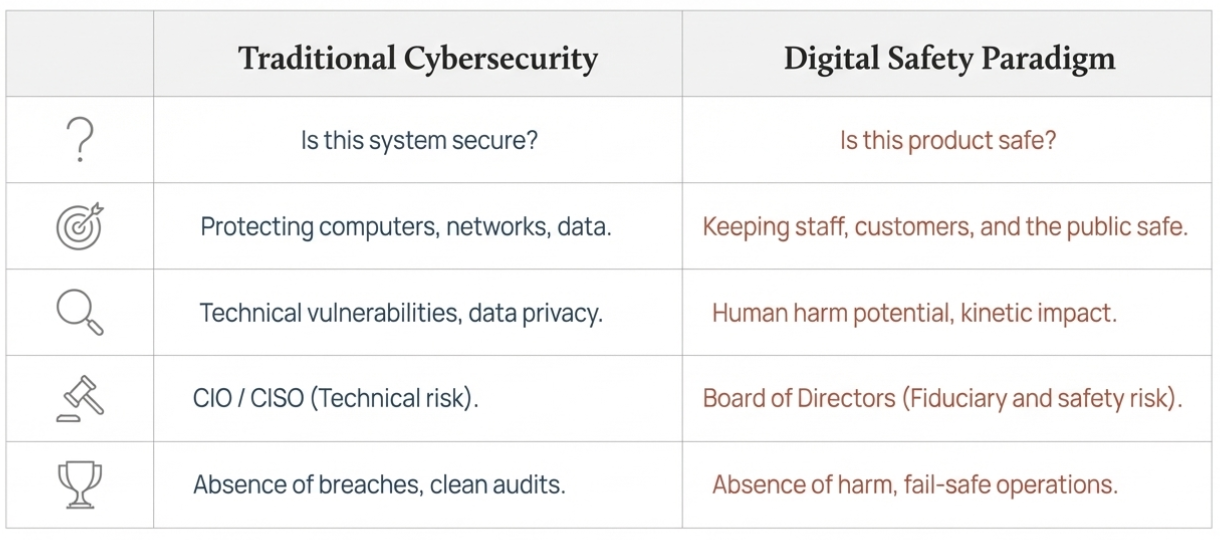
Our decades of real-world, lived, cyber-security expertise bridges technology, people, and critical infrastructure to help ensure that humans remain safe in a modern tech-enabled world. Our expertise spans critical infrastructure, healthcare, and smart tech, ensuring technology is engineered to fail safely, not just to be secure. We help enterprises move beyond outdated security models, focusing on real-world safety for people, data, and operations.


Today’s technology is a complex web of human, AI, and third-party components. We understanding that everyday tech is part of a system-of-systems, and the building of a perfectly secure system today, that stays secure forever is impossible, or at least infeasible. We design for resilience, anticipating that vulnerabilities will emerge—ensuring your systems fail safely, not catastrophically.

We prioritize real-world safety—protecting privacy, finances, and most importantly physical well-being. Our approach centers on people, ensuring technology is not just secure, but truly safe for every user. Physical safety is our "line in the sand". We see corporates and enterprises everyday risk-accept their customers' privacy and finances, balancing the costs to fix against the likelihood of an event. We say that "it's unacceptable to risk-accept someone getting hurt", and we love working with customers who agree on this!

In sectors where digital risks can endanger lives—healthcare, smart cities, and beyond—we embed safety at every layer. Our expertise ensures that human harm is never an acceptable outcome.
We love to question "what does digital-safety and conversely digital-unsafety mean?".
What is a digitally-unsafe home? A home where you're finances and family's privacy is not safe? A home where your smart-front-door or garage door can be remotely unlocked? A home where your smart appliances can be overloaded and cause a fire? We challange that today, it's practically impossible to know the cyber-security posture of all devices in your home / school / office /factory / hospital / vehicle.. and therefore how do you know how digital-safe or unsafe you are?
We move beyond outdated security models to champion digital-safety for interconnected, human-centric systems. Our approach anticipates failure, prioritizes resilience, and designs for safe outcomes—protecting people, data, and critical operations in a world where risk is constant.
We guide enterprises through the complexities of cyber-physical environments. Our experts address hidden vulnerabilities, architect for safe failure, and ensure your technology is robust, adaptive, and ready for tomorrow’s risks.
![[interface] screenshot of cybersecurity dashboard interface (for an ai cybersecurity company)](https://cdn.prod.website-files.com/695acb52e6ef6f1b4fc3cf26/695acb52e6ef6f1b4fc3cf2b_c6a72ee4-033d-4938-b0f1-8b452f53f056.avif)
“Qubit Cyber challenged our thinking on digital safety. Their team helped us design for resilience, not just compliance, and prepared us for the realities of interconnected healthcare systems.”
“Partnering with Qubit Cyber transformed our risk approach. Their pragmatic strategies made our water infrastructure safer, anticipating both human and technical vulnerabilities.”